
Each technical advance brings wave after wave of security holes. Every new protocol may come with exploitable programming errors. Logic errors, vendor-installed backdoors, and default configurations possess the nuisance value to plague everything from modern operating systems to the simplest print server. Moreover, viruses of past seem much paler and tamer as compared to today’s highly optimized Internet worms. Gartner’s estimate that by 2020, 30% of Global 2000 companies will have been directly compromised by an independent group of cyber activists or cyber criminals, then, baths in the light of sense.
This “sure” fear of unknown rightly cries for the need to build an organizational strategy that addresses all the risk indicators. Network administrators need to be equipped with the necessary tools and knowledge to identify vulnerable systems and resolve their security problems before they can be exploited. That’s where the importance of vulnerability assessment, a risk management process, sneaks in.
" Network administrators need to be equipped with the necessary tools and knowledge to identify vulnerable systems and resolve their security problems before they can be exploited. "
The Meaning of Vulnerability Assessment:
In technical lexicon, the word vulnerability denotes any programming error or misconfiguration that could allow an intruder to gain unauthorized access. It could be anything from a weak password on a router to unpatched programming flaws in exposed network services. In simple words, vulnerability assessment is the process of locating and reporting these vulnerabilities. It creates a possibility for you to detect and resolve security problems before they get exploited by someone with a malicious intent. It undertakes it by identifying, evaluating, estimating, and prioritizing expected vulnerabilities.
Subscribe now for valuable insights!
The Importance of Vulnerability Assessment:
However unfortunate it may sound, the general idea of network and overall infrastructure security doesn’t go beyond patch management and antivirus software. People tend to overlook the need to look into configurations and third-party applications’ issues. It doesn’t appear to them that hardware, with its faulty configuration, can inflict irreparable damage on network’s security. Note that 81% of breaches leveraging hacking techniques (misconfigurations, vulnerabilities or exploits) used stolen or weak passwords in 2017, up from 63% in 2016. What it unequivocally implies is even after you have secured your network by fully patching it and deploying antivirus solution, hackers can realize their vile motives by exploiting misconfigurations. Following list highlights issues that a typical operating system installation may have:
- Unnecessary open shares
- Unused user accounts
- Unnecessary open ports
- Rogue devices connected to your systems
- Dangerous script configurations
- Servers allowing use of dangerous protocols
- Incorrect permissions on important system files
- Running of unnecessary, potentially dangerous services
Along with these misconfigurations, vulnerability assessment pinpoints various security issues with a wide range of software and hardware including:
- Default passwords on certain devices
- Unnecessary services running on some devices
- Running web services that contain known vulnerabilities
- Dangerous applications such as peer-to-peer applications
- Third-party applications that are a vulnerability to known exploits
"It’s important to understand that antivirus systems are not almighty. If malware is protected by a rootkit, it may sneak in under the nose of antivirus scans. Most of the vulnerability scanners detect malware based on the computer’s behavior rather than actually scanning the files for known malware signatures. Evidently, they can uncover issues that antivirus might miss."
Similarly, vulnerability assessments will identify active accounts which belonged to employees who left or were laid off. Note that if such accounts aren't disabled, potentially disgruntled employees can log in your systems to cause havoc. The same goes for open shares. Open shares with unprotected passwords or open ports is a hint that the system is running a known malware. This will pop up in the scan results of most of the vulnerability scanners.
Implementation of Vulnerability Assessment:
It infers, then, as clearly as daylight that patch management and antivirus protection cannot cover the ground of network security in totality. In fact, the dynamic and ever-evolving nature of IT infrastructure gives the ring of compulsion to the vulnerability assessment process. It indeed fortifies the security wall by running constantly and informing the administrator every time threat is detected. The well-oiled and result oriented steps can give a proper flesh to its implementation.
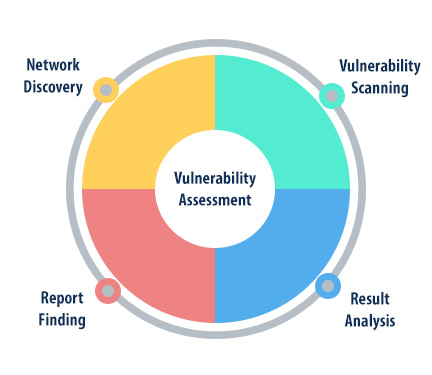
Step 1-Information Gathering & Discovery:
In the first phase, try to gather a detailed understanding of your hardware and software environment. It should include network scanning to discover hosts, port scanning to discover the services and protocols that might be vulnerable, and a review of directory service and DNS information to understand which hosts might be targeted by attackers.
Step 2 - Review:
Once you have understood all the hosts present in the environment, conduct a thorough review of operating systems, applications, ports, protocols and services to gauge the full extent of vulnerability. What should matter the most in this phase is the identification of the version information of organization assets (for example, Windows 10 vs. Windows XP, SMB 3.1.1 vs. SMB 2.0). That’s because succeeding versions often patch old vulnerabilities and introduce new ones.
Step 3 - Detection & Reporting:
The final phase comprises of actual detection of vulnerabilities and use of detection tools or vulnerability repositories like the National Vulnerability Database to identify the vulnerabilities on the assets. It ends up in giving detailed reports, complete with scores and risk information. At the end of this phase, try to use remediation tools to patch, configure, or debug assets as necessary to nullify the detected vulnerabilities.
What to Do After A Vulnerability Assessment?
Once you are done with a vulnerability assessment and have remediated enough findings to improve your security posture, it is necessary to re-examine it freshly. Penetration testing pushes your renewed security setup to the corner to check whether a malicious actor can exploit the smallest vulnerability and gain access to valuable information. Penetration testers will question the assumptions you’ve produced as part of your vulnerability assessment by unleashing a technical attack. In short, it will test the real mettle of your vulnerability assessment by creating a real-attack-like environment.
Subscribe now for valuable insights!